Close

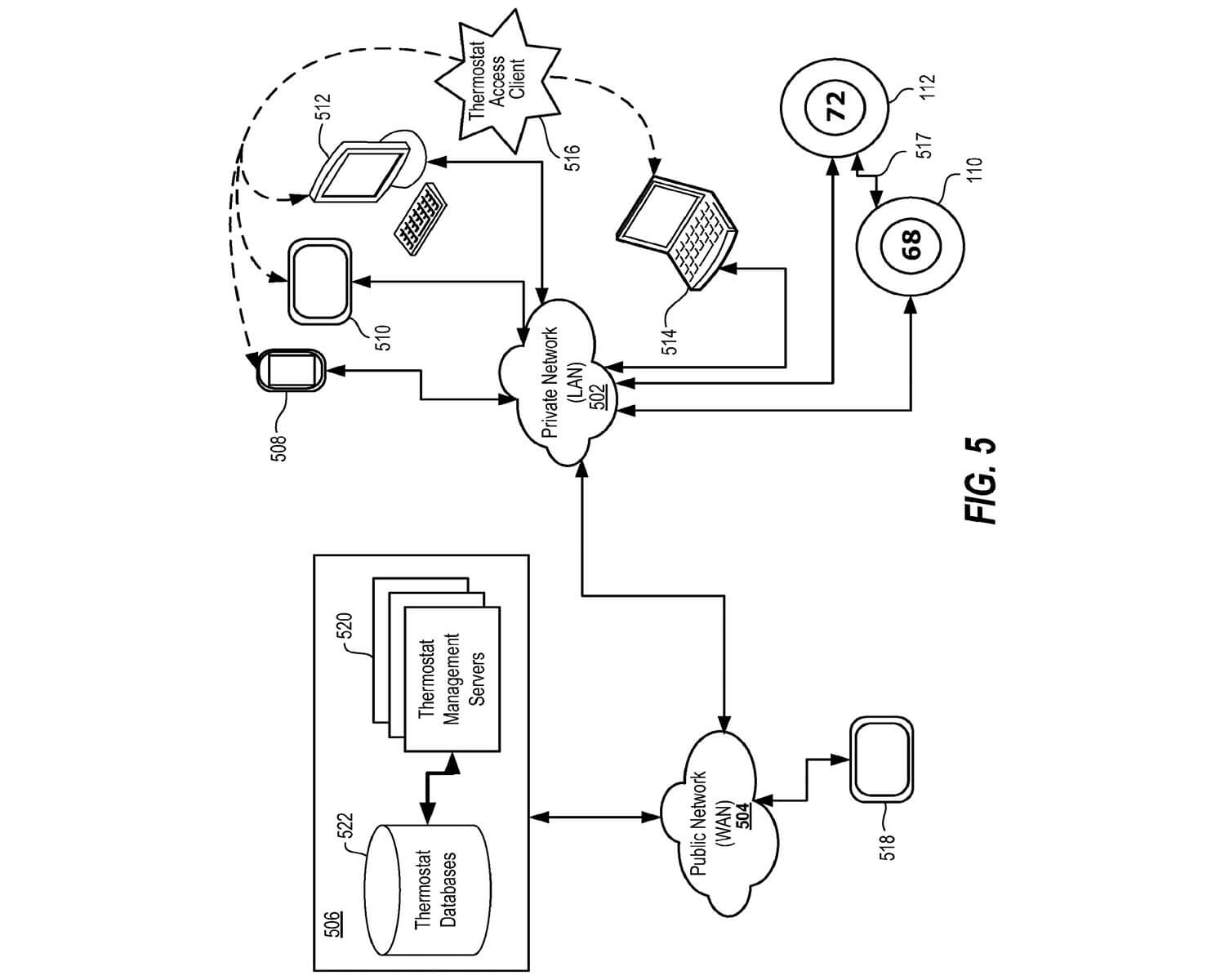
A system for handling and managing critical incidents. System has a mapping module configured to receive alert
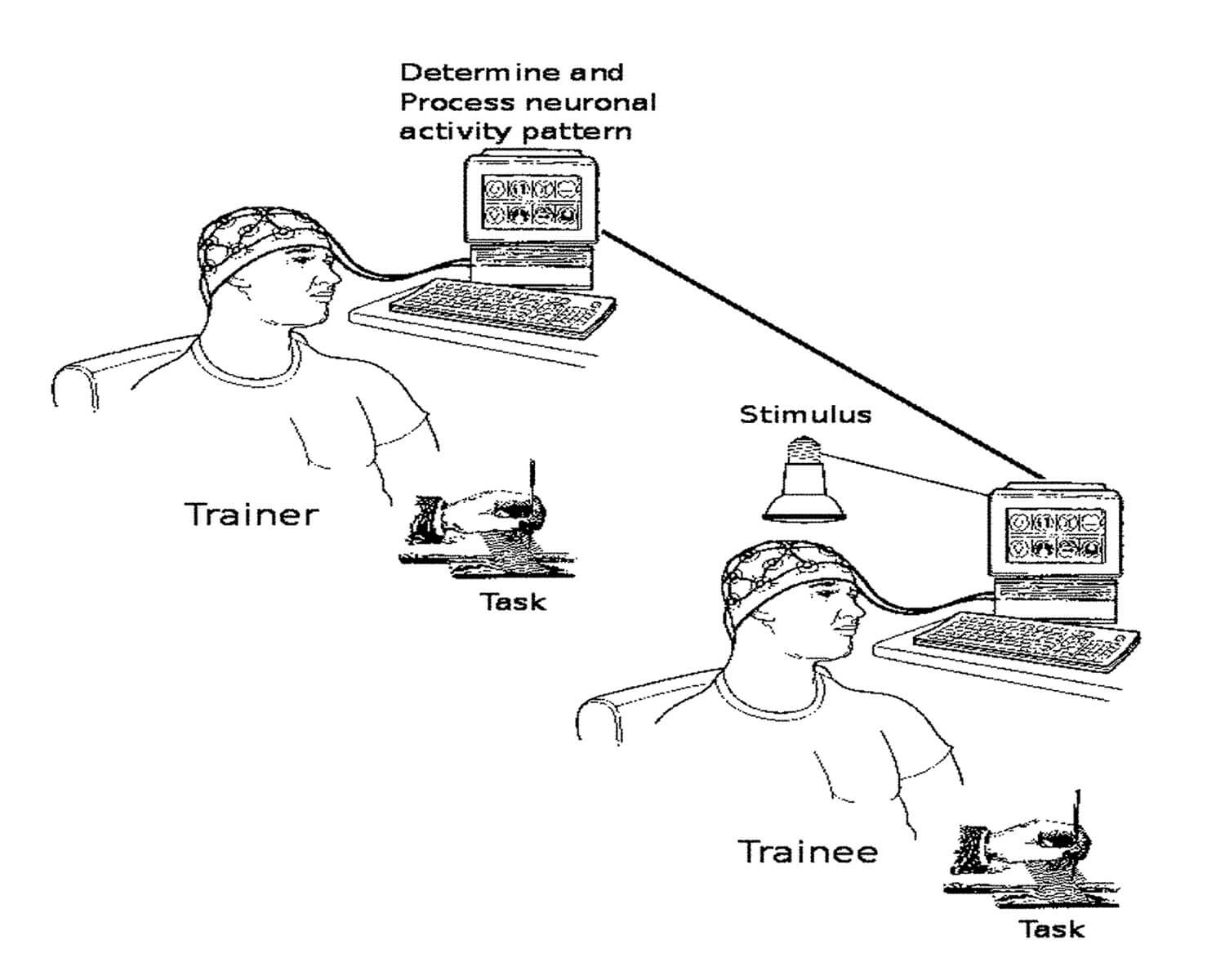
AI-powered virtual being looks and behaves like human beings. Virtual being converse and sympathies
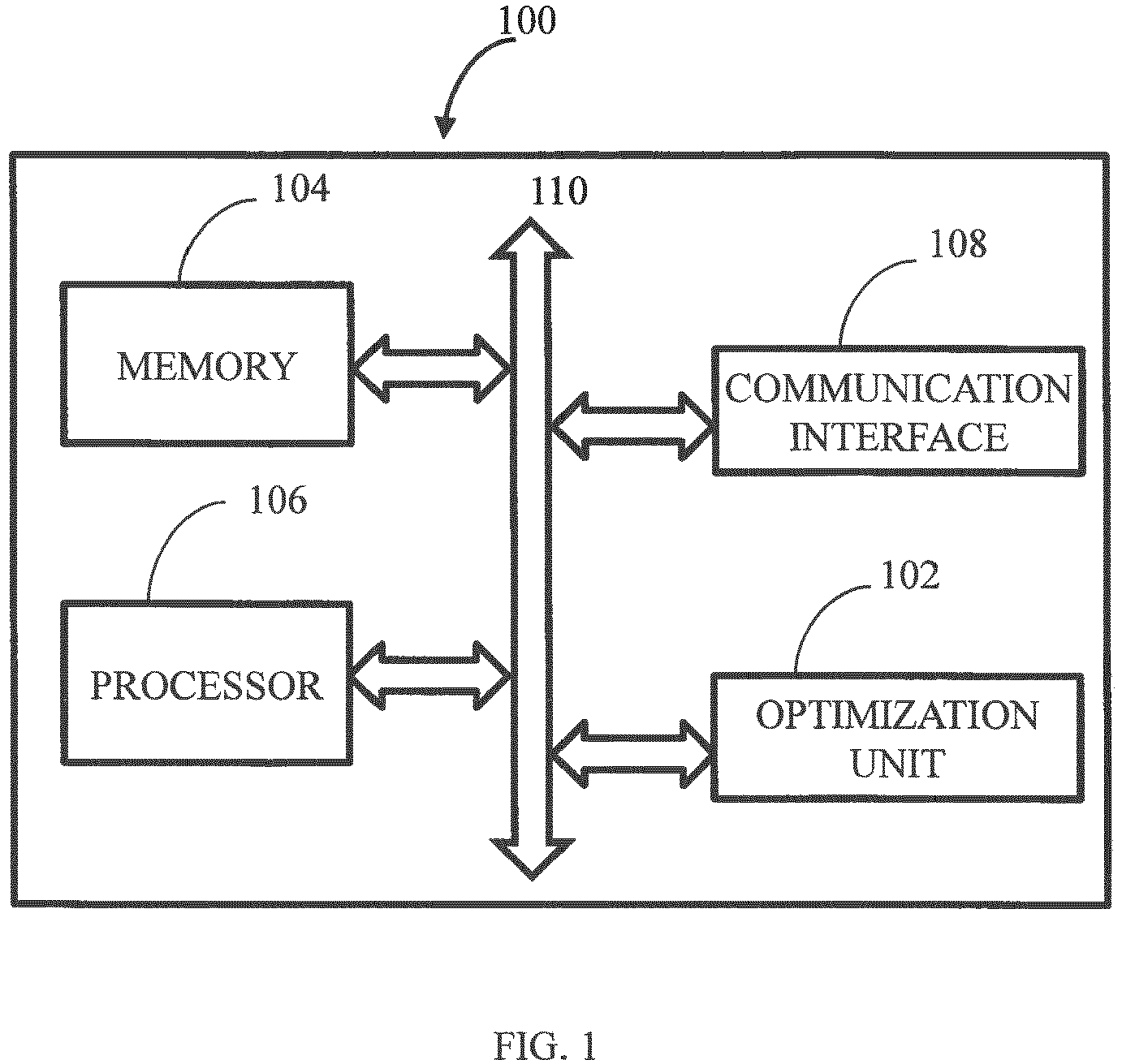
The focus of this study is to investigate novel process and methods for managing databases,

An information processing apparatus for analyzing investment information. An input unit receives a financial request and one or more investment variables...

A diabetes management application having a user interface for representation of data. .....

The invention relates to a method and system for visually annotating an image, comprising: an user interface for presenting digital image. ..

A system for reducing the time for a trader to place a trade. Further, a “Mercury” display and trading method of the present invention ensure fast
Please Subscribe our news letter and get update.
© Copyright 2023 – Wissen Research All Rights Reserved.
Powered by VintageCoders